There is a wide range of hackers: some are just mischievous, testing their skills against your security measures but many want to steal your personal information for more nefarious reasons such as selling on or accessing important accounts. According to the UK Government’s 2014 cybersecurity survey, 81% of large businesses have suffered malicious data breaches. That suggests almost one in five didn’t. But how can those companies be sure?
For example, if you leave your diary or phone lying around unattended, you can’t be sure that someone hasn’t sneaked a look and the same is true for cybersecurity. Often the worst cybercriminals are skilled at hiding their tracks so you may not detect any problems until much later.
“In this context, it’s impractical to prove a negative,” said Lenny Zeltser, a senior faculty member at the SANS Institute, where he teaches malware defence and analysis. “A company responding to signs of infection can conclude that it has been breached,” he points out. “However, the lack of visible signs of a compromise doesn’t indicate that the enterprise has not been breached.”
These attackers are after your intellectual property. They want to pilfer your patents, and steal your documents. But professional criminals are also eager to stay inside your system as long as possible, too, siphoning off valuable data such as customer information and credit card details. Whatever the motive, the stealthy attacker will use a variety of tricks to avoid detection. They want to avoid changing anything too much, lest it draw unwanted attention from alert systems administrators.
I entered an old now unused email address that I suspected was part of the big Adobe security breach a few years back and sure enough it reported that it was present on the stolen list of Adobe users.
How do you know?
While each situation is different there are some actions or websites you can use to run some basic checks. There is a website setup by Lenny Selzer – Was Company Hacked? – (a little tongue-in-cheek but useful nonetheless) which does a custom search on Twitter for common hackers’ hash tags so you can check if you are a target or someone is flagging up your company as vulnerable or actually hacked.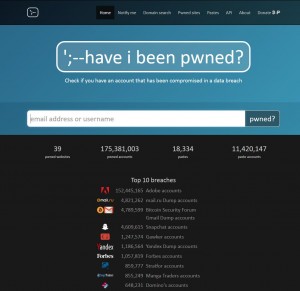
Another very useful service is from Troy Hunt who has taken things a step further with Have I Been Pwned? Instead of looking for social media chatter, this site gathers two sets of data. The first comes from large data breaches that have been publicly disclosed. The second comes from what he calls ‘pastes’.
One of the first places for personal data to appear after it has been stolen is on Pastebin. This site allows people to paste information publicly and anonymously. Many people paste legitimate things on Pastebin such as novels, resignation letters, or their carefully compiled list of every single video game, ever. But others post more contentious documents. Anonymous members have posted missives urging attacks against companies there. And some others post stolen customer details, such as email addresses and encrypted passwords. Lots of them.
I cannot recommend Have I Been Pwned? highly enough. I entered an old now unused email address that I suspected was part of the big Adobe security breach a few years back and sure enough it reported that it was present on the stolen list of Adobe users.
What can you do?
We haven’t really got the space here to go fully into IT and web security measures, but here are some tips:
- Assume that hackers will regularly try to access your computers and network seek and professional advice.
- In terms of your websites and email make sure that you’re hosting with a reputable company and keep your website core files and plugins updated.
- Passwords should be the perfect trade-off between being hard to guess but memorable for the individual.
Get in touch if you if have any questions about Internet security – Contact us or call Dinesh on 07941 686113.
See the original article here: How to tell if you’ve been hacked






